Oracle 数据库安全性评估工具Oracle Database Security Assessment Tool (DBSAT) 可提供专业建议,助您降低 Oracle 数据库的安全风险或漏洞威胁。使用 DBSAT,您可以通过数据库当前状态评估(包括配置)和敏感数据发现等功能,全面洞察数据库的安全和合规态势。DBSAT区分 Oracle on-premises 数据库、自治数据库(共享和专用)和 DBCS,根据数据库目标类型,DBSAT 执行不同的检查项并提供特定于目标的备注。
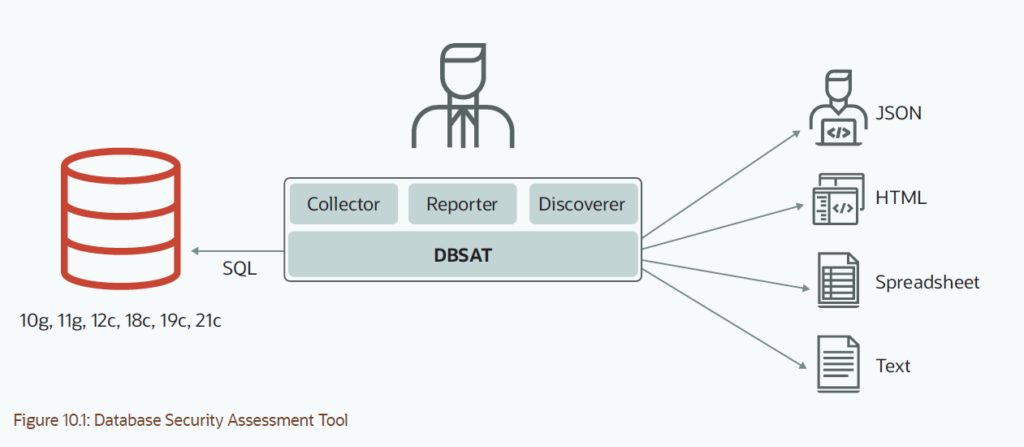
使用方法官方用户手册
Oracle Database Security Assessment Tool (DBSAT) [2138254.1] 下载
DBSAT是仅对oracle安全风险的工具,一套sql+python 编写的脚本命令行工具, 可本地或远程采集(缺失一些OS等本地信息),采集输出json 源数据zip包,执行过程中要求交互输出密码,后期打开zip包需要密码, dbsat reportl输出html,json,excel,txt不同格式报告,如html格式可以在浏览器可读性较好类AWR报告。非常小巧便捷,比国内某绿X感觉更实用。报告中不同颜色识别数据库风险,并给出建议。运行环境需要python 2.6以上,不过像主流版本oracle 19c数据库介质已自带python,目前看是支持10g-21c,测试在23C也OK, 只是不同版本特性检查项还有可能不同。
测试collect, report
安装配置
— 安装下载解压就是一个文件,不再演示, 这里测试的是PDB环境
因为需要使用zip 加密,需要有zip工具
[oracle@db1 tmp]$ ZIP=/usr/bin/zip
[oracle@db1 tmp]$ UNZIP=/usr/bin/unzip
[oracle@db1 tmp]$ DBZIP=${ORACLE_HOME}/bin/zip
比如12c后不带zip, 会提示 Error: /u01/app/oracle/product/2x.0.0/dbhome_1/bin/zip not found.
[oracle@db1 tmp]$ which zip
/usr/bin/zip
[oracle@db1 bin]$ cp /usr/bin/zip /u01/app/oracle/product/2x.0.0/dbhome_1/bin/
创建用户授权
alter session set container=pdb1; grant CREATE SESSION to anbob; grant READ or SELECT on SYS.REGISTRY$HISTORY to anbob; grant SELECT_CATALOG_ROLE to anbob; grant AUDIT_VIEWER to anbob; grant CAPTURE_ADMIN to anbob; grant READ on SYS.DBA_USERS_WITH_DEFPWD to anbob; grant READ on SYS.REGISTRY$HISTORY to anbob;
采集数据
[oracle@db1 tmp]$ ./dbsat collect anbob@172.20.xxx.xxx/pdb1 pdb.out Database Security Assessment Tool version 2.2.2 (June 2021) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Connecting to the target Oracle database... Enter password: Last Successful login time: Wed Mar 01 2023 09:27:33 +08:00 Calling /u01/app/oracle/product/2x.0.0/dbhome_1/bin/zip to encrypt pdb.out.json... Enter password: Verify password: adding: pdb.out.json (deflated 87%) zip completed successfully.
风险分析
[oracle@db1 tmp]$ export PATH=/u01/app/oracle/product/2x.0.0/dbhome_1/python/bin:$PATH [oracle@db1 tmp]$ ./dbsat report pdb.out Database Security Assessment Tool version 2.2.2 (June 2021) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Archive: pdb.out.zip [pdb.out.zip] pdb.out.json password: inflating: pdb.out.json DBSAT Reporter ran successfully. Calling /usr/bin/zip to encrypt the generated reports... Enter password: Verify password: zip warning: pdb.out_report.zip not found or empty adding: pdb.out_report.txt (deflated 80%) adding: pdb.out_report.html (deflated 85%) adding: pdb.out_report.xlsx (deflated 3%) adding: pdb.out_report.json (deflated 83%) zip completed successfully.
on-premises 报告样例
本地部署的报告内容不是很多,整个过程分钟级完成。
包含基本信息,数据库参数,用户profile, 高权用户,长期不登录用户,password 版本及过期、Gradual Password Rollover、default
,用户数据在系统表空间,高权用户及角色,AUDIT, FGA, FGAC, Unified Audit, ACL , TDE,logon trigger, backup, 监听进程, dblink,文件权限等。
Assessment Date & Time
| Date of Data Collection | Date of Report | Reporter Version |
|---|---|---|
| Tue Mar 07 2023 15:00:09 UTC+08:00 | Tue Mar 07 2023 15:07:43 UTC+08:00 | 2.2.2 (June 2021) – 6003 |
Database Identity
| Name | Container (Type:ID) | Platform | Database Role | Log Mode | Created |
|---|---|---|---|---|---|
| ANBOB | PDB1 (PDB:3) | Linux x86 64-bit | PRIMARY | NOARCHIVELOG | Fri Dec 16 2022 16:03:30 UTC+08:00 |
Summary
| Section | Pass | Evaluate | Advisory | Low Risk |
Medium Risk |
High Risk |
Total Findings |
|---|---|---|---|---|---|---|---|
| Basic Information | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| User Accounts | 7 | 1 | 1 | 2 | 1 | 0 | 12 |
| Privileges and Roles | 4 | 17 | 1 | 0 | 0 | 0 | 22 |
| Authorization Control | 0 | 0 | 2 | 0 | 0 | 0 | 2 |
| Fine-Grained Access Control | 0 | 0 | 5 | 0 | 0 | 0 | 5 |
| Auditing | 0 | 8 | 5 | 0 | 0 | 0 | 13 |
| Encryption | 0 | 2 | 1 | 0 | 0 | 0 | 3 |
| Database Configuration | 9 | 3 | 0 | 0 | 0 | 0 | 12 |
| Operating System | 2 | 2 | 0 | 1 | 0 | 0 | 5 |
| Total | 22 | 33 | 15 | 3 | 1 | 0 | 74 |
…
File Permissions in ORACLE_HOME
| OS.FILES | STIG | ||
| Status | Pass | ||
| Summary | Examined 613 files. Found 0 error. | ||
| Details |
ORACLE_HOME: /u01/app/oracle/product/23.0.0/dbhome_1 ORACLE_HOME owner: oracle Directories: 6 (0 permission errors) Executables in $ORACLE_HOME/bin: 230 (0 permission errors) Configuration files in $TNS_ADMIN: 0 (0 permission errors) Data files in $ORACLE_HOME/dbs: 3 (0 permission errors) Libraries in $ORACLE_HOME/lib: 374 (0 permission errors) |
||
| Remarks | The ORACLE_HOME directory and its subdirectories contain files that are critical to the correct operation of the database, including executable programs, libraries, data files and configuration files. Operating system file permissions must not allow these files to be modified by users other than the ORACLE_HOME owner and must not allow other users to directly read the contents of Oracle data files. | ||
| References | Oracle Database 12c STIG v1 r10: Rule SV-76001r1, SV-76277r1, SV-76359r1, SV-76365r1 |
|
|
测试discover 发现敏感数据
这个组件在表和列上查找敏感数据,该组件是有java开发语言编写的JAR包,如果是RAC它只需要在其中一个节点上运行。需要首先设置JAVA_HOME和1.8版本后的JRE环境,但同样ORACLE 安装介质中自带了JDK, 但是需要我们创建一个配置文件.
配置JAVA_HOME
否则会提示Error: Environment variable JAVA_HOME is NOT set to a valid JAVA installation.
[oracle@db1 tmp]$ export JAVA_HOME=/u01/app/oracle/product/23.0.0/dbhome_1/jdk [oracle@db1 tmp]$ ./dbsat discover Database Security Assessment Tool version 2.2.2 (June 2021) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Usage: dbsat collect [ -n ] <database_connect_string> <output_file> dbsat report [ -a ] [ -n ] [ -g ] [ -x <section> ] <input_file> dbsat discover [ -n ] -c <config_file> <output_file> Options: -a Report with all user accounts, including locked and schema-only, Oracle-supplied users -n No encryption for output -g Show all grants including Common Grants in a Pluggable Database -x Specify sections to exclude from report (may be repeated for multiple sections) -c Configuration file for discoverer
配置文件
[oracle@db1 tmp]$ ls ./Discover/conf/
sample_dbsat.config sensitive_de.ini sensitive_en.ini sensitive_fr.ini sensitive_nl.ini
sensitive_el.ini sensitive_es.ini sensitive_it.ini sensitive_pt.ini
[oracle@db1 conf]$ cp sample_dbsat.config my_dbsat.config
[oracle@db1 conf]$ ll
total 236
-r--r--r-- 1 oracle oinstall 5902 Mar 7 17:46 my_dbsat.config
-r--r--r-- 1 oracle oinstall 5902 Aug 17 2021 sample_dbsat.config
-r--r--r-- 1 oracle oinstall 29090 Aug 17 2021 sensitive_de.ini
-r--r--r-- 1 oracle oinstall 12642 Aug 17 2021 sensitive_el.ini
-r--r--r-- 1 oracle oinstall 31911 Aug 17 2021 sensitive_en.ini
-r--r--r-- 1 oracle oinstall 26829 Aug 17 2021 sensitive_es.ini
-r--r--r-- 1 oracle oinstall 27287 Aug 17 2021 sensitive_fr.ini
-r--r--r-- 1 oracle oinstall 25172 Aug 17 2021 sensitive_it.ini
-r--r--r-- 1 oracle oinstall 26302 Aug 17 2021 sensitive_nl.ini
-r--r--r-- 1 oracle oinstall 27424 Aug 17 2021 sensitive_pt.ini
[oracle@db1 conf]$ chmod 750 my_dbsat.config
[oracle@db1 tmp]$ vi Discover/conf/my_dbsat.config
修改文件
###########################################################
#Use DB_HOSTNAME, DB_PORT and DB_SERVICE_NAME to connect using
#password at the prompt
#DB_IP is the IP address or FQDN for the DB Server
#default is localhost
DB_HOSTNAME =172.20.xxx.xxx
#DB_PORT is the port at which the DBSAT tool needs to connect to
#default is 1521
DB_PORT = 1521
#DB_SERVICE_NAME is the service Name for the DB
#default is empty
DB_SERVICE_NAME = pdb1
###########################################################
采集数据
[oracle@db1 tmp]$ ./dbsat discover -c ./Discover/conf/my_dbsat.config pdb_discover Database Security Assessment Tool version 2.2.2 (June 2021) This tool is intended to assist you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Enter username: anbob Enter password: DBSAT Discover ran successfully. Calling /usr/bin/zip to encrypt the generated reports... Enter password: Verify password: zip warning: pdb_discover_report.zip not found or empty adding: pdb_discover_discover.html (deflated 72%) adding: pdb_discover_discover.csv (deflated 30%) Zip completed successfully.
— 因为我的库是新库,如果数据库较大,这步可能会有点时间长。
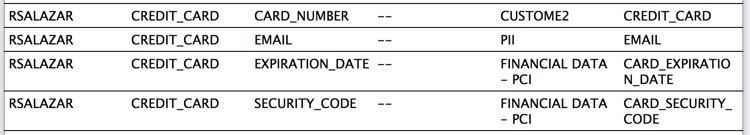
根据预定义的模式可以匹配出像EMAIL, CARD NUM, TELNUM等敏感数据,也可以增加自定义,报告同样是加密码,以html样式
报告样例:
Oracle Database Sensitive Data Assessment
Assessment Date & Time
| Date of DBSAT Report Generation | DBSAT Discoverer Version |
|---|---|
| Tue Mar 07 2023 17:49:51 | 2.2.2 (June 2021) |
Database Identity
| Name | Container (Type:ID) | Platform | Database Role | Log Mode | Date Created |
|---|---|---|---|---|---|
| ANBOB | PDB1 (PDB:3) | Linux x86 64-bit | PRIMARY | NOARCHIVELOG | Fri Dec 16 2022 16:03:30 |
Discovery Parameters
| Parameter | Values |
|---|---|
| Schema Scope | ALL |
| Exclusion List File | NONE |
| Minimum Rows Count | 1 |
| Pattern File(s) | sensitive_en.ini |
Summary
No Sensitive Data discovered
如果有会像下图提示:
数据库安全当然也不只这些,但感叹oracle 的解决方案是如此完善。有安全等保问题欢迎咨询www.anbob.com。
— over —
